I make and sell BusKill laptop kill cords. Monero is accepted.
- 20 Posts
- 17 Comments

 2·9 months ago
2·9 months agoVery nice. Unfortunately it doesn’t look like Boost is available on F-Droid.

 4·9 months ago
4·9 months agoFortunately, in my case, my image was “orphaned” and never actually attached to a post or comment, so it wouldn’t have federated.
If the image has already federated then that’s a whole next level problem :(

 9·9 months ago
9·9 months agoHi, unfortunate author here 😅
The issue happened in Jerboa. I opened a few tickets in the Jerboa app’s GitHub to address this:
- jerboa #1361: UI for deleting uploaded files
- jerboa #1362: Setting to hide "upload media" button
- jerboa #1363: Add "confirm upload" step to UX
Can you please tell us which Lemmy client apps you use that store the delete token and have a UI to delete uploaded images?
 1·9 months ago
1·9 months agoThis is a big problem. At the time of writing:
- Users cannot delete their images on Lemmy
- If a user deletes their account, their images don’t get deleted
- There is no WUI for admins to delete images on Lemmy
- It is very difficult for admins to find & delete images on Lemmy (via the CLI)
- The Lemmy team didn’t bother documenting how admins can delete images on Lemmy
How to purge images in Lemmy
pict-rs is a third-party simple image hosting service that runs along-side Lemmy for instances that allow users to upload media.
At the time of writing, there is no WUI for admins to find and delete images. You have to manually query the pict-rs database and execute an API call from the command-line. Worse: Lemmy has no documentation telling instance admins how to delete images 🤦
For the purposes of this example, let's assume you're trying to delete the following image
https://monero.town/pictrs/image/001665df-3b25-415f-8a59-3d836bb68dd1.webpThere are two API endpoints in pict-rs that can be used to delete an image
Method One: /image/delete/{delete_token}/{alias}
This API call is publicly-accessible, but it first requires you to obtain the image's `
delete_token`The `
delete_token` is first returned by Lemmy when POSTing to the `/pictrs/image` endpoint{ "msg":"ok", "files":[ { "file":"001665df-3b25-415f-8a59-3d836bb68dd1.webp", "delete_token":"d88b7f32-a56f-4679-bd93-4f334764d381" } ] }Two pieces of information are returned here:
- file (aka the "alias") is the server filename of the uploaded image
- delete_token is the token needed to delete the image
Of course, if you didn't capture this image's `
delete_token` at upload-time, then you must fetch it from the postgres DB.First, open a shell on your running postgres container. If you installed Lemmy with docker compose, use `
docker compose ps` to get the "SERVICE" name of your postgres host, and then enter it with `docker exec`docker compose ps --format "table {{.Service}}\t{{.Image}}\t{{.Name}}" docker compose exec <docker_service_name> /bin/bashFor example:
user@host:/home/user/lemmy# docker compose ps --format "table {{.Service}}\t{{.Image}}\t{{.Name}}" SERVICE IMAGE NAME lemmy dessalines/lemmy:0.19.3 lemmy-lemmy-1 lemmy-ui dessalines/lemmy-ui:0.19.3 lemmy-lemmy-ui-1 pictrs docker.io/asonix/pictrs:0.5.4 lemmy-pictrs-1 postfix docker.io/mwader/postfix-relay lemmy-postfix-1 postgres docker.io/postgres:15-alpine lemmy-postgres-1 proxy docker.io/library/nginx lemmy-proxy-1 user@host:/home/user/lemmy# user@host:/home/user/lemmy# docker compose exec postgres /bin/bash postgres:/#Connect to the database as the `
lemmy` userpsql -U lemmyFor example
postgres:/# psql -U lemmy psql (15.5) Type "help" for help. lemmy=#Query for the image by the "alias" (the filename)
select * from image_upload where pictrs_alias = '<image_filename>';For example
lemmy=# select * from image_upload where pictrs_alias = '001665df-3b25-415f-8a59-3d836bb68dd1.webp'; local_user_id | pictrs_alias | pictrs_delete_token | published ---------------+--------------+---------------------+----------- 1149 | 001665df-3b25-415f-8a59-3d836bb68dd1.webp | d88b7f32-a56f-4679-bd93-4f334764d381 | 2024-02-07 11:10:17.158741+00 (1 row) lemmy=#Now, take the `
pictrs_delete_token` from the above output, and use it to delete the image.The following command should be able to be run on any computer connected to the internet.
curl -i "https://<instance_domain>/pictrs/image/delete/<pictrs_delete_token>/<image_filename>"For example:
user@disp9140:~$ curl -i "https://monero.town/pictrs/image/delete/d88b7f32-a56f-4679-bd93-4f334764d381/001665df-3b25-415f-8a59-3d836bb68dd1.webp" HTTP/2 204 No Content server: nginx date: Fri, 09 Feb 2024 15:37:48 GMT vary: Origin, Access-Control-Request-Method, Access-Control-Request-Headers cache-control: private referrer-policy: same-origin x-content-type-options: nosniff x-frame-options: DENY x-xss-protection: 1; mode=block X-Firefox-Spdy: h2 user@disp9140:~$ⓘ Note: If you get an `
incorrect_login` error, then try [a] logging into the instance in your web browser and then [b] pasting the "https://<instance_domain>/pictrs/image/delete/<pictrs_delete_token>/<image_filename>" URL into your web browser.The image should be deleted.
Method Two: /internal/purge?alias={alias}
Alternatively, you could execute the deletion directly inside the pictrs container. This eliminates the need to fetch the `
delete_token`.First, open a shell on your running `
pictrs` container. If you installed Lemmy with docker compose, use `docker compose ps` to get the "SERVICE" name of your postgres host, and then enter it with `docker exec`docker compose ps --format "table {{.Service}}\t{{.Image}}\t{{.Name}}" docker compose exec <docker_service_name> /bin/shFor example:
user@host:/home/user/lemmy# docker compose ps --format "table {{.Service}}\t{{.Image}}\t{{.Name}}" SERVICE IMAGE NAME lemmy dessalines/lemmy:0.19.3 lemmy-lemmy-1 lemmy-ui dessalines/lemmy-ui:0.19.3 lemmy-lemmy-ui-1 pictrs docker.io/asonix/pictrs:0.5.4 lemmy-pictrs-1 postfix docker.io/mwader/postfix-relay lemmy-postfix-1 postgres docker.io/postgres:15-alpine lemmy-postgres-1 proxy docker.io/library/nginx lemmy-proxy-1 user@host:/home/user/lemmy# user@host:/home/user/lemmy# docker compose exec pictrs /bin/sh ~ $Execute the following command inside the `
pictrs` container.wget --server-response --post-data "" --header "X-Api-Token: ${PICTRS__SERVER__API_KEY}" "http://127.0.0.1:8080/internal/purge?alias=<image_filename>"For example:
~ $ wget --server-response --post-data "" --header "X-Api-Token: ${PICTRS__SERVER__API_KEY}" "http://127.0.0.1:8080/internal/purge?alias=001665df-3b25-415f-8a59-3d836bb68dd1.webp" Connecting to 127.0.0.1:8080 (127.0.0.1:8080) HTTP/1.1 200 OK content-length: 67 connection: close content-type: application/json date: Wed, 14 Feb 2024 12:56:24 GMT saving to 'purge?alias=001665df-3b25-415f-8a59-3d836bb68dd1.webp' purge?alias=001665df 100% |*****************************************************************************************************************************************************************************************************************************| 67 0:00:00 ETA 'purge?alias=001665df-3b25-415f-8a59-3d836bb68dd1.webp' saved ~ $ⓘ Note: There's an error in the pict-rs reference documentation. It says you can POST to `/internal/delete`, but that just returns
404 Not Found.The image should be deleted
Further Reading
Unfortunately, it seems that the Lemmy develoeprs are not taking these moral and legal (GDPR) risks seriously (they said it may take years before they address them), and they threatened to ban me for trying to highlight the severity of this risk, get them to tag GDPR-related bugs, and to prioritize them.
- lemmy #4433: Deleted Account should delete uploaded media (pictures) too
- lemmy #4441: Users unable to delete their images (pictrs API)
- lemmy #4434: Unapproved users cannot delete their accounts/data
- lemmy #3973: Banned users cannot delete their accounts/data
- lemmy #4445: Create an interface for local users to view and remove images
- lemmy-ui #2359: Allow users to delete images they uploaded
- lemmy-ui #2360: Allow admins to view & delete uploaded images
- lemmy-ui #2361: private_message_disclaimer to include user's matrix handle
- jerboa #1361: UI for deleting uploaded files
- jerboa #1362: Setting to hide "upload media" button
- jerboa #1363: Add "confirm upload" step to UX
- lemmy-docs #293: Document image moderation
If GDPR-compliance is important to you on the fediverse, then please provide feedback to the Lemmy developers in the GitHub links above.
Attribution
This comment was copied from the following article: Nightmare on Lemmy Street (A Fediverse GDPR Horror Story)
Nightmare on Lemmy Street (A Fediverse GDPR Horror Story)
 1·9 months ago
1·9 months agoThis seems to suggest that you have to get it from lemmy when you first uploaded the image
 5·9 months ago
5·9 months agoThanks, but I’m asking because I didn’t find the reference documentation especially helpful.
It says I need the “delete token” or “alias”. How do I get that for a given URL?
I’m looking for an example that describes how to construct the commands for the API calls knowing only the URL of the image.
You definitely can do that, but if you’re afraid that you might stand-up and forget you’re using it, then you probably shouldn’t.
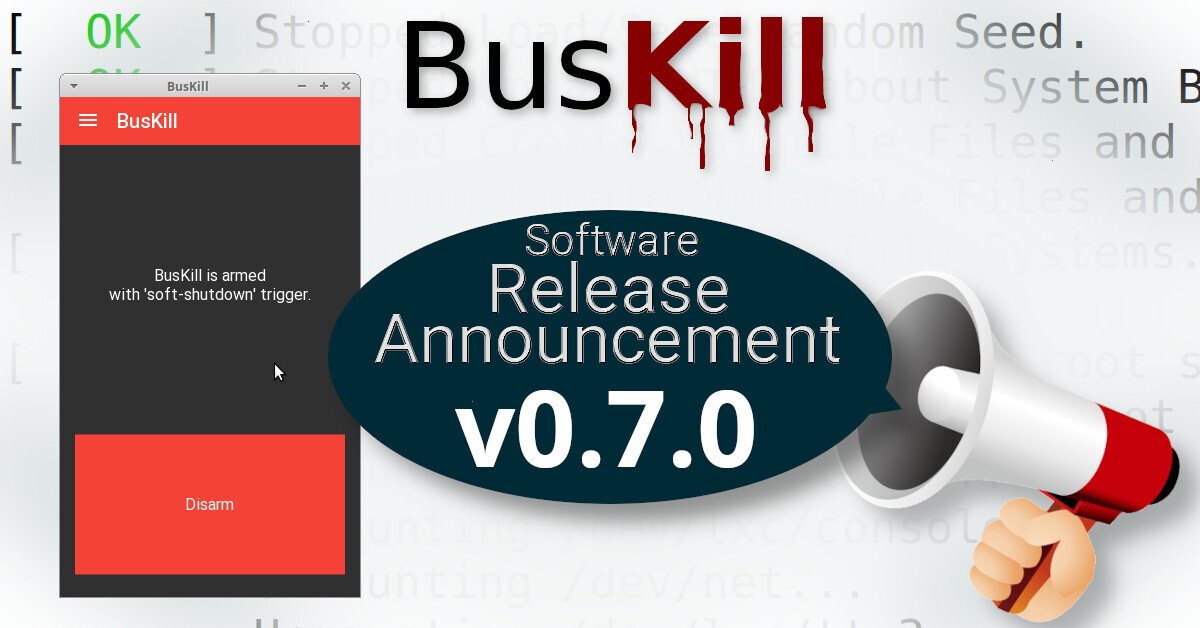
It’s probably enough to just use the default trigger that locks your screen. Or, once you get comfortable with it, set it to shut down your computer. Most people don’t need to shred their FDE keys, unless they’re facing torture.
In fact, we make it difficult to use “destructive” triggers (like the LUKS Header Shredder that wipes the FDE header) and intentionally do not include the ability to switch to it in the app. To use it, you have to do a lot of extra work. So most users don’t have this issue.
Why? It defaults to just locking your screen. So you stand-up, the magnetic breakaway cable separates, and then you just have to type your password…
If you’re the type of person that would forget to lock your computer before standing up and walking away, then it’s exactly what you’d want.

 34·1 year ago
34·1 year agoYes, it’s clearly disclosed in my profile that I am the founder of the BusKill project.
This is a PSA that our sale has started. I’ve had inquiries from members of our community asking about Black Friday sales.
10% off is barely any discount anyway.
Sorry, we’re a very small open-source shop. I’ve paid myself nothing so-far. The price just barely breaks-even for the business.
All of this is explained in-detail in “The Finances” section here.
Prices would drop dramatically if we could do production runs (and actually sell) >10,000 units at a time. Currently we only sell a few cables per month. If you want to help, please tell all your security-conscious friends about BusKill :)

 38·1 year ago
38·1 year agoHi, this is not spam but a useful PSA that’s full of information, not just about the sale.
BusKill is useful for many groups, including human rights defenders, activists, journalists, whistleblowers, etc. You can read more about the use-cases of our community at our documentation here:

 42·1 year ago
42·1 year agoYes, BusKill works with any USB drive.
In fact, the BusKill cable is just a USB Drive. The only thing “fancy” that it has is a magnetic coupler in the middle of the 1-meter cable so that it will breakaway at any angle. But, if you’d like, you can build your own. The instructions are here:

 31·1 year ago
31·1 year agoI’ve paid myself nothing so-far. The price just barely breaks-even for the business. There’s one-time costs like a few grand for a CNC’d injection mold and assembly jig, but also certification fees, product boxes, cardstock paper for documentation inserts, printing fees, artist commissions, packaging materials, warehousing, shipping, other logistics fees, etc.
All of this is explained in-detail in “The Finances” section here.
I prefer open-source hardware to be designed using common off-the-shelf items that are easily found everywhere in the world. Unfortunately, the one vendor of a USB-A magnetic breakaway couplers decided to EOL their product shortly after I published a guide on how to build your own BusKill cable. After we published, they all got sold-out, and we had to go to manufacturers for a custom component.
Prices would drop dramatically if we could do production runs (and actually sell) >10,000 units at a time. Currently we only sell a few cables per month. If you want to help, please tell all your security-conscious friends about BusKill :)

 2·1 year ago
2·1 year agoIt should only be posted once to this community. It’s also been cross-posted to other relevant communities.

 11·1 year ago
11·1 year agoUnfortunately, that’s what it costs to make open-source hardware at small-scale.
There’s a cheaper $59 cable available or you could build your own.

 7·1 year ago
7·1 year agoGood bot
 01·1 year ago
01·1 year agoI’m curious if any security engineers have covered this incident.
Stripe does support generating Restricted API Keys. With “Restricted API Keys” you’re able to mint a key that can live on your e-commerce website that has permission to accept payments but does not have permission to modify your merchant account’s payout methods (eg adding a new “Instant Payments” debit card to the merchant account as this attacker did).
Unfortunately, I’ve asked WooCommerce to support Restricted API Keys 1 year ago, but they marked it as “low priority”
…I would appreciate if more people would jump-in on ^ that ticket and scold WooCommerce so that they add support for Restricted API Keys ;)













Hi, Michael Altfield here. I was the sysadmin for OSE from 2017-2020.
Everything OSE does is transparent, so you can just check the OSE websites to see what everyone is currently working-on. OSE contributors log their hours in a worklog called “OSE Dev”. There you can quickly see who is working on what.
The above graphs show 4 contributors in the past ~10 weeks (one is me; we had some issues with the apache config recently). There’s no direct link, but you can then check the wiki to see people’s work logs (just search for the person’s name and
Log):I also like to look at the MediaWiki “Recent Changes” page to peak at what people are up-to as well:
I told Marcin about Lemmy back in June 2023. Another OSE contributor even created an OSE community on the slrpnk.net instance, but it appears to have been abandoned. I’ll email him about this thread to see if he’ll bite and publish updates in this community since there’s clearly interest :)
Also, shameless plug: I started an org that’s very similar in spirit to OSE called Eco-Libre, with a focus on projects to sustainably enfranchise human rights in smaller communities. We’re currently accepting volunteers ;)